Environment based encryption
Why you need Confisense:

★ Confisense allows for safe transportation or storage of data within the public space* and allows for the opening of data in specific locations only.
★ Remote communication is secured by means of a unique key exchange powered by the elliptic curve cryptographic algorithm and symmetric encryption.
★ This allows a sender and a receiver to interact with a secured file while maintaining a private security channel between the sender and receiver.
★ The Eccenscia Security Network validates the software installation and verifies the validity of the user’s software.
★ Our anti-tampering algorithm verifies each of the files that make up the Confisense software, including generated configuration files to detect any tampering that may have occurred.
* Public space is defined as anywhere outside of the local ecosystem.
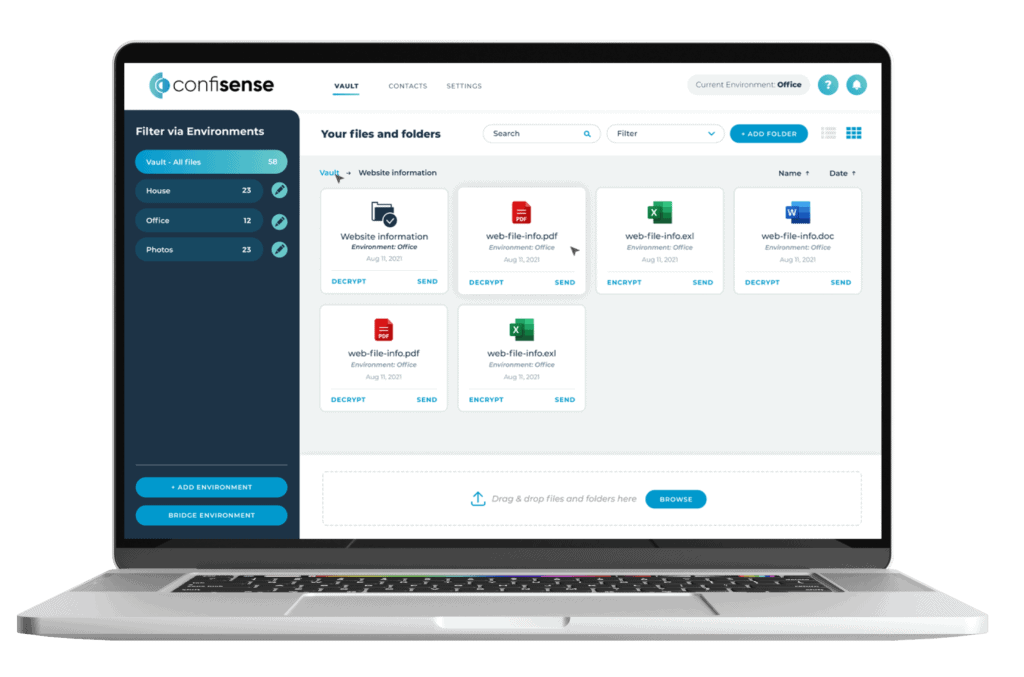

You dont need to have an IT degree to use the solution. It is quick and easy to setup. Don’t believe us? Try the free version.

Files and folders are protected and may only be open by the recipient at their specified environment, location or workplace. The user’s environment is scanned and evaluated using Eccenscia proprietary environment authentication algorithm. The algorithm does allow for non-consistency in ever changing environments.

Cryptographic keys are at the heart of security on any digital system. Owning your own key gives you the ability to manage your own security. It is private to you and you alone.

Data Security Algorithms used have never been hacked (NIST-P256 elliptic curve cryptographic algorithms). The elliptic curve algorithm has been implemented for secure key exchange. Data is encrypted, signed and verified, which prevents data manipulation and secured transport of sensitive data.

Contact information is provided to a 3rd party on request and user approval only. This places the security 100% in the user’s control. Self-managed contacts ( dual authenticated contacts) .

Confisense adds environmental authentication , identity verification and access authorization with Uloq technology.

Your personal vault is a protected area in Confisense where you store your private and sensitive files.

Encrypt or secure a file over public channels for a specific contact that cannot be decrypted by anyone else except by your specified contact.

Files sent via emails, or even social media can be served via end to end encryption.

Users are notified if changes are made on encrypted OR DECYPTED? file on their device and can approve or deny the changes. Each of the files which make up the Confisense software are hashed and compared to our security network database. This reduces the risk of tampering on a stolen computer.

Uloq Integrated for remote authentication, verification and authorization (files may only be unlocked by the receivers once authorisation has been given by the data owner). Remote authorisation using Uloq. This allows the user to verify their environment using a remote key. The key incorporates personal identification using fingerprint or password, does the environmental scan. They keys are registered on the Eccenscia Security Network and the environment verification is done on the Confisense software.

You don’t need an IT degree to use Confisense. It is quick and easy to setup. Don’t believe us? Try the free version. TRY IT FREE!

Files and folders are protected and may only be open by the recipient at their specified environment, location, or workplace.

Cryptographic keys are at the heart of security on any digital system. Owning your own key gives you the ability to manage your own security. It is private to you and you alone.

The Data Security Algorithms used in Confisense are based on NIST-P256 elliptic curve cryptographic algorithms. The elliptic curve algorithm has been implemented for secure key exchange.

Contact information is provided to a 3rd party on request and user approval only. This places the security 100% in the user’s control.

Confisense adds environmental authentication, identity verification and access authorization with Uloq (Mobile App) technology.

Your personal vault is a protected area in Confisense where you store your private and sensitive files.


Encrypt or secure a file over public channels for a specific contact that cannot be decrypted by anyone else except by your specified contact.

Files sent via email, or social media are secured via an end to end encryption.

Users are notified if changes are made on the files in their Confisense Vault. They can approve/decline the changes.

Uloq is integrated with Confisense for remote authentication, verification, and authorization.
Personal vault
Encryption
Decryption
Uloq Keys
Environments
Bridged Environments
Secured Contact
Remote decryption verification (Uloq)
Data recovery phrase
User owned keys
Business
Principles | Verify explicitly | Least Privilege | Assume breach |
|---|---|---|---|
What it means | Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies | Limit user access with just-in-time and just-enough-access (JIT/JEA), risk based adaptive policies, and data protection to help secure both data and productivity. | Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defences. |
How we tackle it | 1. Confisense verifies data origination by creating a relationship between senders and receivers. This relationship is verified using key deriving algorithms. 2. Confisense verifies the identity of the user. This is done using Uloq. | 1. Data access is limited by environmental and identity authorization. 2. The configuration files are not accessible to system users. | 1. Access to Confisense can be restricted using Uloq as a second-factor authentication. 2. Application setting changes can be protected and authorized with a Uloq key. (No setups and settings changes are permitted without performing an identity verification using Uloq. ) 3. Files cannot be decrypted without a user being fully identified by Uloq. |
What it means
Verify explicitly
Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies
Least Privilege
Limit user access with just-in-time and just-enough-access (JIT/JEA), risk based adaptive policies, and data protection to help secure both data and productivity.
Assume breach
How we tackle it
Verify explicitly
Least Privilege
Assume breach
Physical Address (Head Office)
ECCENSCIA LLC
Sharjah Media City
Sharjah
UAE
Formation No: 2115999
Email
info@eccenscia.com
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
We’d love to send you more information about Confisense and how you can use it to protect your information.
Please enter your email address to continue.